Mobile Shield
Are you sure your phone is working only for you?
Mobile Threat Landscape
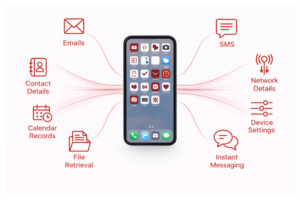
Your smartphone is no longer just a device — it is your office, your identity, your personal moments and your access point to critical systems. It’s a single, always-on device and an ideal target for attackers.
With cyber threats evolving at an unprecedented rate, advanced spyware can attack your device without you even making a click.
Then, they operate in the background, silently exfiltrating your data when your security team struggles to monitor and protect an entire ecosystem of endpoints, devices and networks.
Zero-Click
Attacks
Advanced exploits compromise a device without any action from the user
One-Click
Attacks
Threats are activated when a user is tricked into performing one single action.
Physical & Proximity Attacks
Threats with direct physical or close-range interaction with the device.
Misconfiguration Vulnerabilities
Weaknesses created by insecure device settings and lack of security monitoring
Next generation mobile protection is here

Your smartphone is no longer just a device — it is your office, your identity, your personal moments and your access point to critical systems. It’s a single, always-on device and an ideal target for attackers.
With cyber threats evolving at an unprecedented rate, advanced spyware can attack your device without you even making a click.
Then, they operate in the background, silently exfiltrating your data when your security team struggles to monitor and protect an entire ecosystem of endpoints, devices and networks.
Key Benefits
The Sphynx Cyber Range platform empowers organisations by providing a dynamic, hands-on training environment that equips teams to respond to the latest threats and vulnerabilities. It is designed to prepare your workforce with both broad and specific skills that apply directly to your organisational context.

Real Time Defense

Historical Scans

No Personal Data Access

Fully owned by you

Zero-Day coverage

Security per Role & Exposure
Envoid Scan
Automated and on-demand fleet-wide scanning to identify active and historical mobile compromises.

EnScan Kiosk
Self-service mobile scanning that delivers a clear, clean or compromised result in minutes.

EnScan Kit
Portable mobile forensic scanning for teams operating in the field or on-site.

EnScan Server
Centralized, automated scanning across large fleets with full visibility for security teams.
Envoid Protect
Continuous, real-time protection across mobile fleets, detecting and responding to advanced threats as they occur.

EnPort for Organizational Protection
Centralized mobile threat protection for employee and BYOD device fleets

EnPortable for Single-Device Field Protection
Compact, standalone, real-time mobile protection for individuals on the move

EnTactical for Multi-Device Field Protection
Field-ready protection unit, securing up to 30 devices in fully offline field operations
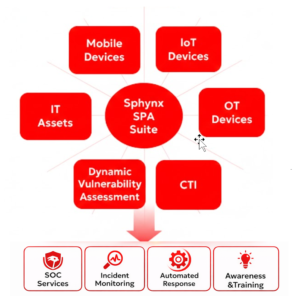
360° Cyber Risk Management with the Sphynx SPA Suite
Mobile Shield powered by Envoid delivers real-time and historical mobile threat detection without accessing personal data, ensuring privacy by design.
By integrating insights with the Sphynx SPA Suite, it extends visibility across IT, OT, IoT and mobile for complete 360° cyber risk management:
- Complete visibility across the entire attack surface with IT, OT, IoT and mobile devices,
- Dynamic vulnerability assessments
- Correlation with premium CTI feeds
- Actionable risk intelligence
- Combined with Managed security Services and Training
- Customizable solution integrating with existing solutions
Resources
Download the Presentation
Ready to elevate your team’s cybersecurity readiness?
Contact us to explore how the Sphynx Cyber Range can provide tailored training to meet your organisation’s unique needs.
Explore your cybersecurity needs and solutions
Our team of experts can assist you in identifying your cybersecurity risks and set up a plan to protect, detect, and respond to them.
